01.

Vulnerability Assessment
A comprehensive vulnerability assessment provides organizations with the knowledge, awareness and risk background necessary to understand threats to their environment. Remediation measures can then be applied accordingly. Identifying risks before hackers do will drastically improve the cyber security posture of your business.
Penetration Testing
We provide both external and internal pentesting services. External pentest focuses on weakest points, whether the weakest link is the application, the network, or the personnel. Internal pentest mimics an attack originating from inside the company, perhaps from a malignant or disgruntled employee, or a hacker who managed to get inside the internal network.
Web Application Security
Application security is the process of making apps more secure by finding, fixing, and enhancing the security of apps. Much of this happens during the development phase, but it includes tools and methods to protect apps once they are deployed.
1. Native Application
We’re committed to building sustainable and high-quality Java solutions.
2. CMS Testing
We’re committed to building sustainable and high-quality PHP solutions.
3. OWASP Framework
We’re committed to building sustainable and high-quality C++ solutions.
4. Methodology
We’re committed to building sustainable and high-quality Qt solutions.
Mobile Application Security
1. Android Application
We’re committed to building sustainable, secure and high-quality Android Applications.
2. iOS Application
We’re committed to building sustainable, secure and high-quality iOS Applications.
3. Reverse Engineering
We’re committed to building obfuscated Android & iOS Applications.
4. Modern World Techniques
We use modern world attacks to pentest the application during and after development.
Application Testing Methodology
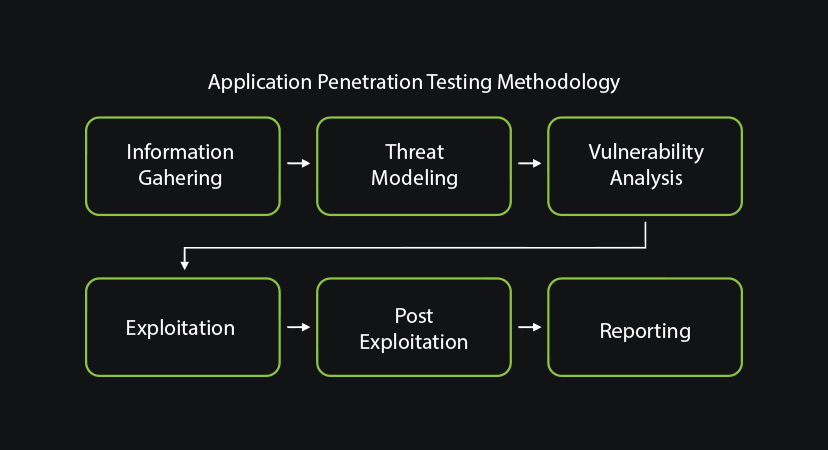
Source Code Review
We have a range of licensed and open-source automated tools to work with its Code Reviews Services. Be it web applications or financial applications, The Brainia ensures the highest standard of coding to assure the best products. Injection flaws to improper error handling, insecure configurations, or session management, our experienced lot can find bugs early and secure any vulnerable codes. From Sample-based Audit of the code to reporting having an outlook for precision is where we are best.
Secure Software Development Life Cycle
A secure SDLC involves integrating security testing and other activities into an existing development process. Examples include writing security requirements alongside functional requirements and performing an architecture risk analysis during the design phase of the SDLC.
LET’S GET STARTED TODAY, SCHEDULE A FREE CONSULTATION WITH THE BRAINIA REDTEAM
At RedTeam Security, we understand the hard work and level of detail that goes into application development (we’re highly experienced developers!), so we know first-hand how easy it can be to miss some security points. Unfortunately, cybercriminals know this. They’ll be waiting to actively seek to exploit these weaknesses through various attack vectors, such as SQL injection, social engineering, phishing, injecting malware, or by exploiting other web application vulnerabilities. To combat these bad actors, we’ll perform a risk assessment and vulnerability assessment to help us fully understand your configurations and identify any potential weaknesses. Once this is achieved, we’ll use our robust testing tools to see how your web application stands up to our pen-testing.
Our goal is to help your team zero in on critical issues, understand any potential security vulnerabilities, and help you to identify solutions to ensure your web applications are the strongest they can be from a security standpoint. Through the vigorous processes established in our testing methodology, our experienced pentesters will find any weaknesses and help you establish solid security controls to prevent future data breaches or other exploits. About 80% of our application penetration testing is manual testing, with 20% being automated vulnerability scan testing. To learn more about web application security testing, schedule your free virtual meeting with a RedTeam Security expert today at +92-304-8342501.



